Adam's RSA Trip Report
This year, I had a great opportunity. I got to travel to the RSA Conference and be both an attendee and also help represent Science of Security and Privacy at the agency’s booth. I tried to update the VO each day of the conference, but I found I didn’t have the time or the energy to accomplish that. Instead, I’m writing this trip report.
Onto the trip.
Day 1, Monday. First day at RSA. It started as many conferences do, picking up ones badge. It’s a little more complicated than I expected. Turns out that the Moscone Center in San Francisco is more like a collection of buildings rather than a unified convention center. I knew the booth was in Moscone South, so that’s where I started. Turns out Moscone West is where registration is. After a city block walk away (I assume I went west), I found the building.
They had turned the entire first floor into the registration area. If there were seats it would hold like 10,000. Seemed like over kill for registration, there was hardly anyone around. Step one was to walk through the path of rope line and go to a computer. It verified I was registered and told me what one of 30 registration desks to go to. Seemed like an unnecessary step as no one was in those lines anyway. Get to the registration desk and they have my badge ready for me. Oh, so the time I was walking, my badge was printing. Very industrial engineering there, keep me busy so I don’t see the wait. I asked about my expo hall pass, they didn’t know anything about that and so I was directed to the exhibitors help desk. New set of desks to visit. They were helpful, saw that I had both registrations in the system and updated my badge. In reality, I didn’t get two badges, but rather the color of the bottom of the badge holder was changed. Initially it was green and “Full Conference” printed on it. With the exhibitor recognition, it became blue with “Full Conference.” I was set. With the blue tag, I could enter the exhibit hall early and leave it late. Oh, before leaving the registration area, a stop at the materials table. There they scanned the badge, must be a registration chip inside. Pretty sure its NFC because they were using cell phones to read it. The flow of the registration room didn’t seem as orchestrated here. The person took the conference backpack put the conference materials in it and then got a shirt of the appropriate size. With all the planning on flow, I kinda expected the bags to be premade and ready for pickup.
Now it’s time to work. So walk back to Moscone Center South, The exhibit hall in below surface. Security is making sure everyone has blue badges. Either Exhibitor ones or Full Conference. Get down there, find where the booth is it’s a little bit of adventure. It’s sensory overload. It’s like a casino. Each 20x20 foot booth has lights, screens, and sounds. Everyone is trying to get your attending and buy their product. It’s amazingly large. And this is just the south hall, there are 2 more. I get to the booth, and everything is ready. It is really nice not to be the one in charge and responsible. Everything is taken care of. I just have to do my part.
At 5p, the hall opens to outside attendees and visitors pretty much come immediately. The next 2 hours are the welcome reception in the exhibitions halls. The halls were active, people milling about the booths, a few snacks carried by servers in the aisles, people with drinks. I talked with people about SoS. The main focus seemed people looking for alcohol or free trinkets. Neither of these were in our booth. This opening session lasted 2 hrs. It doesn’t sound long, and it really wasn’t that long. But I was tired afterwards.
One thing we did was make a schedule for the next day for the 3 of us to rotate through the booth.
  |
Day 2, Tuesday. The booths opened at 10a, but my day started much earlier. The advantage of having a full attendee badge is the opportunity to attend the information sessions. Tuesday included a keynotes from 8a to 1030a. These keynotes were not part of the $100 expo hall pass. I proceeded to get to the Moscone Center around 745a. Plenty of time ahead of 8 right? Not really. The first question was, where were the actual keynotes? Providing the answer were people with RSA flags strapped to their back. Kinda like a backpack. She informed me that the keynotes were in Moscone West, same place as registration. Right. Walked back to West. Lots of people around and entering the hall, keynotes were directed up the escaladers. As I ascended, I could look out at the first floor. The empty registration hall from the day before now had a line the left the room and backed up into the lobby. Good thing I got that badge the day before.
Arriving on the 2nd floor, we were herded past some light refreshments, coffees, teas, juice, and around the floor. Yes, we went around the entire floor and then to more escalators to the 3rd floor. Arriving in the keynote hall, there were people with glowing green wands, as if they were ground crew for aircraft, direction people to available seats. The room was huge with maybe 10,000 seats, and I got a seat 1 row a head of the last. I barely made it into the room.
The Tuesday keynote session started with a music performance. Yes. It was kinda strange. HoTSoS probably can skip that and no one will feel like it was an incomplete conference. Hmm, at looking at the youtube video of it [https://youtu.be/o44aPMskllg] I discovered there were drones with lights. I could not tell that at all where I was sitting. Thought it was just part of the digital background of the stage.
The first real talker was the President of RSA, Rohit Ghai. An engaging speaker, he went with a positive message about silver linings. He tried to say that the cybersecurity aspect is better than before. Look at the silverlings, quick silver solutions, and we have there is no silver bullet. Yes, silver was part of all 3 themes. He tried to be positive. I didn’t buy that the cybersecurity is better; I’m sure most of the other attendees felt the same way. None of the other speakers followed with that message either. He had a second message. Now Matters. That's the theme of RSA 2018. Ie, what happens now matters. Yeah, that theme is in the logo and swag. It wasn't really carried on beyond this opening keynote. Youtube Video: https://www.youtube.com/watch?v=ahpB6n5l_vo
The next talk was Microsoft’s President, Brad Smith. He talked about the importance of people being safe and having privacy. He called for governments to stop cyber attacking civilians in cyberspace, especially in peace. We don’t accept that in the physical world. People are drying, example the Britsih HHS attacks of last summer. Russia attacks disabled much of their computing infrastructure, canceling surgeries and other medical consequences. Microsoft sent a crew out there to get video testimonies about the consequences. They tried to make it personal. He then called for a digital Geneva convention. 6 items: 1. No targeting of tech companies, private sector, or critical infrastructure. 2. Assist private sector efforts to detect, contain, respond to and recover from events. 3. Limit offensive operation to avoid a mass event. 4. Exercise restraint in developing cyber weapons and ensure that any developed are limited, precise, and not reusable. 5. Commit to nonproliferation activities for cyber weapons. 6. Report vulnerabilities to vendors rather than stockpile or sell them. YouTube Video: https://www.youtube.com/watch?v=XGutGYNfEw0
After the RSA talk, was Christopher D. Young, the CEO of McAfee. He decided to go with Plane Hijacking as a metaphore for cybersecurity. Youtube Video: https://www.youtube.com/watch?v=o84J4jhgE6k
Following Chris Young, was a highlight, the Cryptographer’s Panel. This all-star panel of cryptogrpahers was a highlight of the morning. Panelists were Whitfield Diffie, Paul Kocher, Moxie, Ronald Rivest, Adi Shamir. They pretty much talked about their thoughts on the direction of cybersecurity. Whit Diffie, SoS Distinguished Expert for paper competition, who later in the day visited the booth, held up two people who we lost in the past year that had made a great contribution to cybersecurity and both not well known. First was his wife, Mary Fisher. It wasn’t just for her emotional support. Almost everyone in the world loved Mary and that opened doors for him everywhere. The second was Mahlon Doyle (Wiki: https://en.wikipedia.org/wiki/Mahlon_E._Doyle). Mahlon was a retired cryptographer for NSA and before that during WWII worked on SIGSALY. SIGSALY was the voice encrypter that President Roosevelt and Prime Minister Winston Churchill used to communicate. (Wiki: https://en.wikipedia.org/wiki/SIGSALY) Youtube Video: https://www.youtube.com/watch?v=-fpNaapuPGY
The final keynote of Tuesday was Kirstjen Nielsen, Secretary of the Department of Homeland Security. She is definitely a high level government official at RSA. I was surprised to see here there. Maybe it was because I’m used to government information, but I didn’t find noteworthy material. Youtube Video: https://www.youtube.com/watch?v=f6Hp5SQFOXw
After the keynotes, I hurried over to the expo hall to take my first shift at the booth. And wow, the hall was busy. I thought Monday night was the big day, I was wrong. It was crowed with people and notice and energy. Wow. I discovered that there were other government entities there. FBI had a booth and DHS had two booths. The 2nd booth for DHS S&T had two floors! And a videos of Doug Maughan. It was really strange to see video of him on screens.
Lunch was provided by food trucks outside the expo hall. Cheap eats, not exactly. Like $16 for some bbq brisket, a drink and a side. It was ok.
I then went to an information session on the security of wearable technologies. Turns out, the session was kinda awesome. The head of FitBit Security, Marc Brown, was speaker one and the other was John Cook, Sr Product Management of Symantec. It’s great to have such senior people in a small session. Did I learn anything interesting. A few things. One that Fitbit treats the phone as a conduit to the cloud for the trackers. Video: https://youtu.be/lvIUVN7-hOw
After that session, back to the booth for the remainder of the day.
Day 3 - Wednesday - Goal to get better seats; so must get there earlier than the day, 730a arrival, success. Talks being at 8a. Today, I was smart enough to get dropped off by Moscone West. Oh, the keynotes aren’t until 1030a? Ok, so sessions first. The first session I attended was Learning from the Three-Ring Circus of NotPetya. This was a person who talked about what it was like to be a victim of NotPetya. My expectations and the talk was a mismatch. This was mostly organizational lessons learned from the attack. Dull for me. I was more expecting in the trenches discussion of what happened.
The second talk of the morning was in the Marriot. Wait, a 5th location?? Ok, time to find it, turns out, there are whole area part of the Marriot Hotel. This was one block up from Moscone West, and then under a bunch of things. It’s all underground. Finding my way there, I found it. Internet of Wild Things—A Mock Trial. Yes, it was a Mock Trial. I really enjoyed this. How do you do a Mock Trail, RSA Style. 1. Get a federal judge to serve as judge (he had just retired; but done this in perilous years). 2. Get a leading defense attorney. 3. Get a good prosecutor; they got a women who is the council for the minority party in the Senate Intelligence Committee. The case was an IoT device manufacture who made a garment to make VR more physically tactile. Yes, it became popular in the adult VR community. J Now years later, the batteries are exploding and causing injuries. The case had 3 questions be decided. 1. Can this case be a class-action suit. 2. Liability 3. Wasn’t something ever really discussed. They spent much of the time on facts of the case and could it be a class action suit. The class action suit was decided not to be a case for a class action. Why? Because the class would be difficult to determine. The suits had been sold through resellers. The manufacturer didn’t have any customer contact. The manufacturer added an update the firmware capability on later iterations of the suit. That surprisingly had a consequence on liability. No, it wasn’t decided how, but a relevant point. A longer session would have been really helpful, but it was cut short for time. No Youtube Video for this great session.
From the Marriot, went directly to the keynotes. Yes, this means I moved up in the room. Closer to the front. You can see that in the pictures. However, the quality of the keynotes definitely wasn’t as good as the day before.
The keynotes on Wednesday began with a poet doing an oral history of the RSA Conference. It’s really good and I think work the 4min YouTube video watch: https://www.youtube.com/watch?v=8zUYG2g7fDQ
The first major talk was from Cisco’s John Stewart. The main message here was diversity. Need to get more ideas / new ideas to tackled the challenges. He showed that women have become more prevalent in tech, but that trends has not come to cybersecurity. How can we solve the cybersecurity challenge if half the population isn’t involved? He highlighted many programs in getting more youth with diverse thinking involved in cybersecurity. NSA’s GenCyber was one such program. Another message is don’t confuse Hard Work with Results. Youtube Video: https://www.youtube.com/watch?v=ZSFV6t24Yqg
The second keynote was from Symantec’s Samir Kapuria. I should mention, in the pictures you see all the fancy lighting. Yes, there were fog machines to help the beams of light be visible. There are also circle suspended from the ceiling for additional dramatic effect. Most of the time the colors were shades of blue. However, they were changed for specific companies. Symantec, is known for yellow, and the room was bathed in yellow lightings. McAfee is red, and the room had an ominous red shade. To the Symantec Message. He talked about scale, and using AI as a force multiplier. It was not so noteworthy. YouTube Video: https://www.youtube.com/watch?v=9nUz58RqjsA
And then the panel. This panel of Alan Paller’s was with 3 other top SANS experts and they discussed the 5 most dangerous attacks techniques. They also did questions, and did it well for such a large audience. Made people email question in during it. So, the 5 are: 1. Repositories and Cloud Storage Leakage. 2. Big Data Analytics, De-Anonymization and Correlation. 3. People want to use your CPU power to mine Bitcoin over data theft. 4. Hardware Attacks 5. CPS attacks. Youtube Video: https://www.youtube.com/watch?v=aoIPIIB4xlA
Before booth working, off to lunch at another food truck. Fried Chicken and Waffles. Channeling the SoS Team Lead there.
Finally, the day had a session on doing cybersecurity awareness. It was different, it wasn’t lecture format. Instead it was the group sitting around a table discussing cybersecurity awareness. Main message, we need to make the messaging funny. People remember funny. Just don’t miss, missing on funny is worse then not being funny. Interesting message for future SoS work. Try to be more funny. Hmm.
Closed out the day at the booth. And another day at RSA is over.
 See much closer I am today. |
 GenCyber!! Woohoo! |
 SANS Panel |
 Fried Chicken and Waffles for Lunch. Salad was sad. |
Day 4 - Thursday - Final Day
The push is on. I don’t care about the 3 hrs time change. The long days and especially the early mornings are wearing on me. This morning was a struggle to get up and there at RSA for the first session at 800a. But I’m really glad I did. This morning I experienced two engaging sessions.
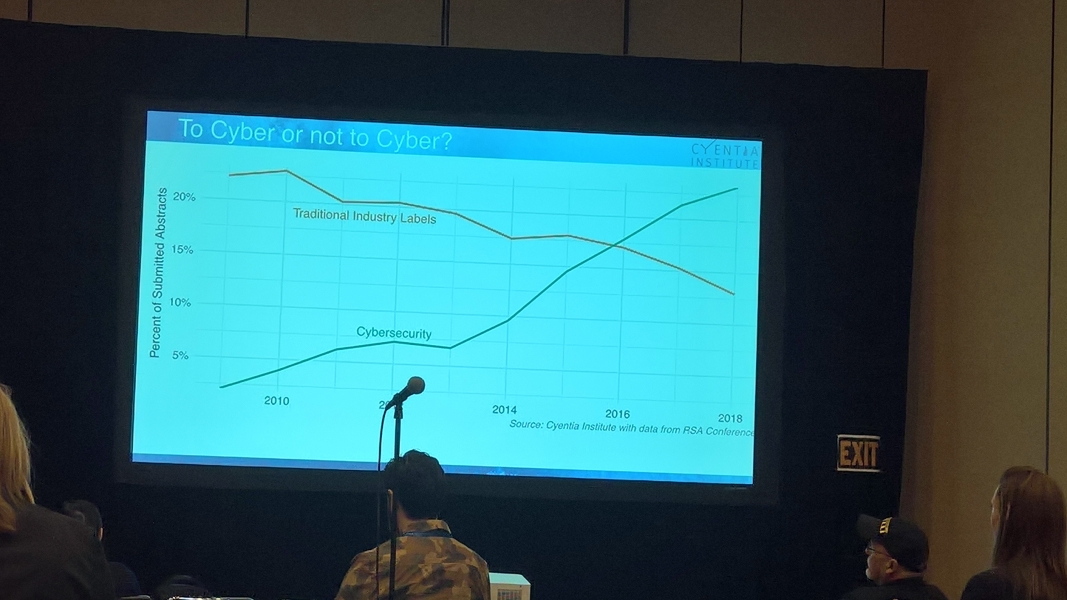
First up was definitely the more academic research talk of the entire trip. These researchers decided to study the abstracts for all submitted papers to RSA over the past 10 years. This was a way to see the trend of ideas at RSA and the cybersecurity industry. The research was fascinating in the many different ways to automatically examining the over 10,000 text documents. One I liked, was the rise of cyber in the vocabularty. At 2009 it was about 0, now 25%. That has exceeded the traditional industry labels. Instead of badly describing all the analysis, I found a report in the topic: https://go.rsaconference.com/rsac365-inb/auth-wadebaker-securitygold
The second was about hacking in healthcare. So this was an intense session. The idea was that these three hacking were going to demonstrate the real impact of a cyber attack in the healthcare industry. Ok, but the twist is that instead of just talking about it, they decided to hold a training simulation with an unaware ER doctor. So this ER doctor was going to treat a patient. They had simulation actors for all the other personnel including the patient. They brought a patient in with an issue of high blood pressure. It was pretty benign case. Expect the drug pump instead of pumping the drugs over a course of a few hours did it immediate. The patient then had an overdose. The doctor saved the patients life.
This was all very medical TV intense. However, where the session felt short, (only post reflection) was that ideas for solutions was super weak. Effectively was that medical device manufactures need to do better at security and patching. Umm, that wasn’t a big hit. It reinforces the idea that you need to have follow through and need to tell the audience what you want them to do. URL: https://www.rsaconference.com/events/us18/agenda/sessions/9887-hacking-healthcare-live-bits-and-bytes-meet-flesh
Keynote time. Go directly to the keynote and this time, I had the best seat of all. Within the front 10 rows. J So much closer. What I learned was that there was a huge gap between the stage and the audience. Perhaps for the cameras. Even though I pretty much at the front, there was still a good gap to the presenters.
Introduction by the poet/comedian again. He did some humorous jokes/stabs to some of the exhibitors. https://www.youtube.com/watch?v=rWyFqLG8BZk
First up was two speakers from Akamai. Andy Ellis, Chief Security Officer, and Josh Shaual, VP Websecurity. It was interesting and informative, but the presentation was a bit awkward. They went with a kinda QnA style between the two. It was highly scripted and it showed. But the content was there. They talked about Akamai’s approach to dealing with security and getting access further to the perimeter. The first thing they did was replacing passwords and treat all devices as outside the network. Instead of internal and external devices, they thought of everything as external. This opened up employees from working from anywhere, not just on company networks. As to replacing passwords, they had certificates and then prompts on cell phones about allowing access.
There were only two session in this short keynote, but the second was noteworthy. It was Tim Urban creator of the website Wait But Why. This was totally on procrastinating. He was very funny and as a reflection of the previous session on cybersecurity awareness, people remember humor. I remember this session. Just watch the video, no, don’t wait, just watch it. : https://www.youtube.com/watch?v=EAGGCHCNDss
Lunch time, tofu bahmi from another food truck. Good but not great.
Then the afternoon at the booth. Doing the last sessions of the day.
I did take some time in the afternoon to see some other booths. Microsoft had a Microsoft Security Blanket. RSA had a giant booth. One booth had an escape "room" More like a large box. Yes, team NSA escaped.
And RSA wound down. At the end, it was packing the boxes of extra materials to ship back and use at ISEF. And anti-climatic, it was over.
Lessons Learned from the Trip
- Well. I learned that if you go to RSA, going to the sessions makes it much more rewarding then just working the booth or expo hall. I’m really glad I was able to do both. Some sessions are really interesting and the prestige of the presenters is outstanding.
- I learned there is a big disconnect from industry to academia and research. RSA feels much about buying and selling. Ok, really about getting free things from booths. But research barely makes it there
- In the future, investigate selling agency ware. I think people will buy it. FBI and DHS has things for sale.
- I learned that in future SoS participation, show off, teach people about some result. Have a message that you want people to do. You might get some to bite
- Don’t park in San Francisco. That’s pretty obvious and not something I did. It’s expensive for the day. Looked like $50+. But I could see it would be not a good idea. Not to mention car break ins are a thing. One night, we parked by one of the piers. Got back, and the police were around another car. They told us that 10 cars were broken into that night. We found empty pocketbooks and laptop bags under our car. Glad we took the time to hide everything, and add trash to the back to make it look sloppy and empty.
- Cable cars are not free.
- Get up and go to the early sessions, it’s worth it.
Well, that’s my trip report. I’m sure you probably haven’t read this far, but if you have, congrats. And go watch the video on procrastination, stop… umm.. procrastinating.