-
 "NSF Backs Rice Processor Design, Chip Security Research"
"NSF Backs Rice Processor Design, Chip Security Research"The National Science Foundation (NSF) has awarded Rice University computer scientists two grants to explore new information processing technologies and applications.
-
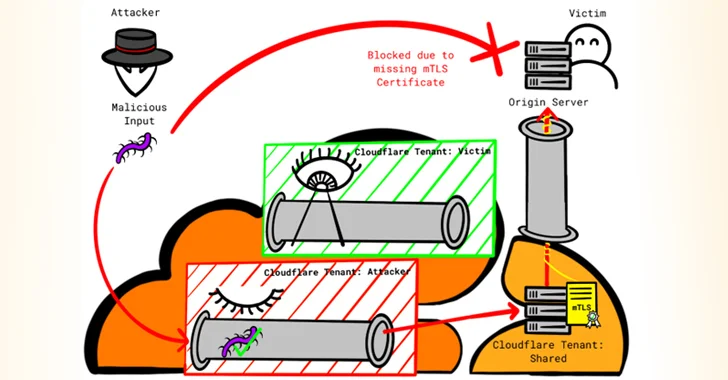 "Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection"
"Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection"Cloudflare's firewall and Distributed Denial-of-Service (DDoS) attack prevention mechanisms can be circumvented by exploiting gaps in cross-tenant security controls.
-
 "Growth in Cybersecurity Spending Sank by 65 Percent in 2022-23, Report Finds"
"Growth in Cybersecurity Spending Sank by 65 Percent in 2022-23, Report Finds"According to a new report from IANS Research and Artico Search, there was a 65 percent drop in cybersecurity spending growth during the 2022-23 budget cycle.
-
 "Upstream Supply Chain Attacks Triple in a Year"
"Upstream Supply Chain Attacks Triple in a Year"Security experts at Sonatype have warned of surging cyber risk in open-source ecosystems, having detected three times more malicious packages in 2023 than last year.
-
 "FBI Warns of Surge in 'Phantom Hacker' Scams Impacting Elderly"
"FBI Warns of Surge in 'Phantom Hacker' Scams Impacting Elderly"The FBI gave a public service announcement warning of an increase in phantom hacker scams targeting senior citizens throughout the US.
-
 "Motel One Discloses Ransomware Attack Impacting Customer Data"
"Motel One Discloses Ransomware Attack Impacting Customer Data"Budget hotel chain Motel One Group recently announced that some customer information and credit card data was stolen in a recent ransomware attack.
-
 "Zero-Day in Arm GPU Drivers Exploited in Targeted Attacks"
"Zero-Day in Arm GPU Drivers Exploited in Targeted Attacks"A vulnerability, tracked as CVE-2023-4211, in the kernel drivers for several Mali GPUs "may be under limited, targeted exploitation," the British semiconductor manufacturer Arm confirmed when it released drivers updated with patches.
-
 "Iran-Linked APT34 Spy Campaign Targets Saudis"
"Iran-Linked APT34 Spy Campaign Targets Saudis"A phishing campaign that spreads cyber espionage malware is aimed at users in the Middle East. The campaign is conducted by the Advanced Persistent Threat (APT) tracked as APT34, also known as OilRig, Helix Kitten, and Cobalt Gypsy.
-
 "Time-To-Exploit: What It Means and Why It's Going Down"
"Time-To-Exploit: What It Means and Why It's Going Down"According to researchers, the average time it takes threat actors to exploit vulnerabilities before or after their public disclosure continues to decrease.
-
 "Machine Learning Technologies Revolutionize Security"
"Machine Learning Technologies Revolutionize Security"Integrating Machine Learning (ML) technologies into different security aspects has brought a new era of proactive threat detection, risk mitigation, and improved decision-making processes.
-
 "Critical Vulnerabilities in Exim Threaten Over 250K Email Servers Worldwide"
"Critical Vulnerabilities in Exim Threaten Over 250K Email Servers Worldwide"According to researchers, thousands of servers running the Exim mail transfer agent are vulnerable to attacks involving the exploitation of critical vulnerabilities that enable remote execution of malicious code with little or no user interaction.
-
 "Security Researchers Believe Mass Exploitation Attempts Against WS_FTP Have Begun"
"Security Researchers Believe Mass Exploitation Attempts Against WS_FTP Have Begun"Researchers suspect the mass exploitation of vulnerabilities in Progress Software's WS_FTP Server. Researchers at Rapid7 first observed evidence of exploitation across multiple instances of WS_FTP on September 30.
News